Validate SSL Certificate & Private Key

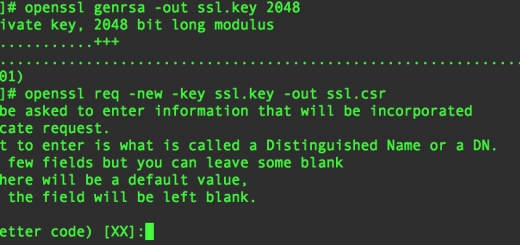
It’s not uncommon to need to validate if an SSL certificate / private key combination is valid. The easiest way to do this is with OpenSSL, an open source library that…
is a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It is also a general-purpose cryptography library.
A an example use case commonly you will need to prepend intermediate certificates to your SSL certificate before installing it – for example in the case of GoDaddy certs – so it’s nice to have a way to check to make sure the pair will work correctly once it is deployed.
Using openssl we can generate an MD5 hash from both the certificate and keys, and the resulting MD5 hashes should match if the pair is valid. The private key was created when you generated the CSR for your SSL provider.
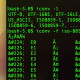
openssl x509 -noout -modulus -in CERTIFICATE.crt | openssl md5 openssl rsa -noout -modulus -in CERTIFICATE.key | openssl md5
If this is a task that you perform routinely you can use a bash script to further automate the process. In this example script, if your certificates and private keys have common prefixed names with different extensions then it will automatically calculate and compare the MD5 of each. You will likely want to expand the functionality from here – feel free to share any improvements you have made!
CERT=certificate_name CERT_CRT=$(openssl x509 -noout -modulus -in $CERT.crt | openssl md5) CERT_KEY=$(openssl rsa -noout -modulus -in $CERT.key | openssl md5) if [[ "$CERT_CRT" = "$CERT_KEY" ]]; then echo "yes"; else echo "no"; fi